There has been a far greater responsibility on the Chief Information Officers(CIOs) to understand the challenges, solutions and trade-offs in […]
Currently browsing: Blog
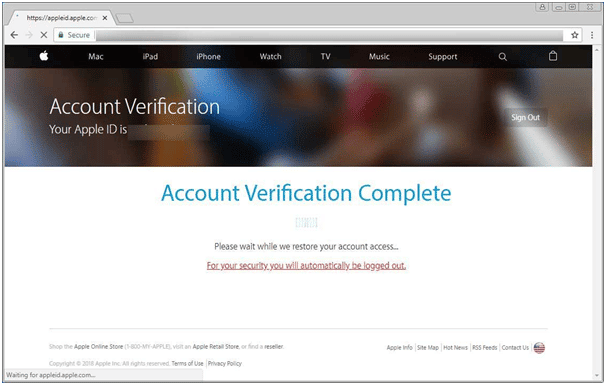
Widespread Apple ID Phishing Attack Pretends to be App Store Receipts
This is big, the Apple-ID which managed to stay away from compromises is under attack. A notorious phishing campaign is […]
Are the e-commerce sites cyber-safe?
Can there be someone else in your shopping cart? Well, the scenario does sound scary but it might very well […]
Economic Impact of DMARC for companies across the globe
What is DMARC? DMARC is a security standard which allows a domain to declare a policy of how it wants […]
Concerns of SMBs on DMARC
DMARC (domain-based message authentication, reporting and conformance) has been gaining traction over the past couple of years. Organisation familiarising themselves […]
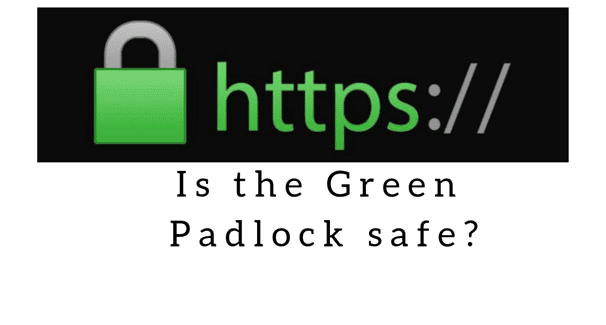
Half of the Phishing sites trick users by displaying the green padlock!
Phishing has always been hackers favorite act. It allows them to make multiple rewards after they succeed. Not only it […]
Business e-mail compromise (BEC), the new service which has takers!
For as low as $150 you can get the credentials for an email account. Hackers in some advert claim the […]
Increasing Phishing attacks in India
Phishing is on the rise in the country. India is among the top 4 countries in the world for Phishing […]
Latest DNS Spoofing attacks use fragmented datagrams. Can you avoid it?
With a little attention, as it turns out, one can spoof fake DNS responses using fragmented datagrams. How is it […]
Prevent the Fileless Attacks for your Windows PC
What is a Fileless or non-malware attack A non-malware attack is one in which an attacker uses existing software, allowed […]