This is big, the Apple-ID which managed to stay away from compromises is under attack. A notorious phishing campaign is underway that pretends to be a purchase confirmation from the Apple App store. This has come to light recently and seems to be a classic phishing campaign and interestingly it has gone widespread quickly since the way this is engineered is fairly simple. The Apple account holders receive emails which contain a PDF attachment that pretends to be a receipt for an app that was purchased by their account for $30 USD and then asks the person to click a link if the transaction was unauthorized. Of course the transaction is unauthorized because the user hasn’t done that. Once a user clicks the link, they are hacked!
The campaign plays a very simple tone and doesn’t even asks users to open the pdf. It is by nature a person will look into the purchase if he hasn’t made one. The email contains a PDF attachment that states it’s a receipt for the purchase, but there is nothing telling you to open the attachment. Instead the attackers are relying on the victim’s inquisitiveness here and which seems to work well.

When a user opens the PDF they will be shown what appears to be a receipt from Apple for an app that they purchased. Sprinkled throughout the PDF are links that the recipient can use to report a problem or that the purchase was unauthorized. All of these links are for a shortened URLs so a recipient does not know the URL of the page that it ultimately goes.

When a user goes on to click on the link they will be redirected to a page that asks them to login with their Apple ID. This page is identical to Apple’s legitimate Apple Account management portal. The URLs for the page however are same as apple but only an observant victim may become suspicious.

The hackers don’t stop here and give another push if the victim feels suspicious. If a user does enter their login information they will be brought to a page stating “This Apple ID has been locked for security reasons. You must unlock your account before signing in.”

With this message when a user clicks on the Unlock Account button. Here is the real deal, now the user is more or less convinced and hackers asks for all the details to verify the account here. The page shown next asks the user to verify their account information so that the account can be unlocked. This page asks for the victim’s full name, address, telephone number, social security number, date of birth, payment information, and security questions that include your mother’s maiden name, driver’s license number, or passport number.

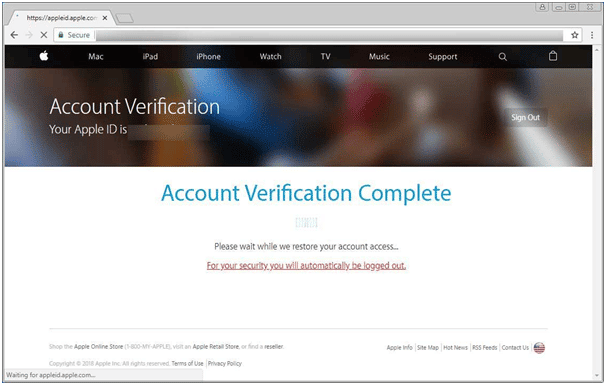
When a victim finishes entering the information and submits it, they will be brought to a temporary page states that the user will be automatically logged out in order to restore access to their account.

The phishing page will then redirect you to the legitimate appleid.apple.com account management page. The brilliant part is that they do so in a way that causes Apple’s site to display a message stating “This session has timed out for your security”. This further corroborates the phishing page’s story that you were being logged out to recover your account and that this is all a normal and expected process.

On the off chance that a victim had entered their data, the assailants will presently have enough to play out an entire recognize robbery of the person in question. This incorporate opening bank or charge card accounts, getting to different records with the data, or documenting government forms under the unfortunate casualty’s name.
This is an extremely broad and progressed phishing effort that uses pages that seem to be indistinguishable to the genuine Apple account pages and brain science that keeps on illustration an unfortunate casualty through the different screens of this assault. Because of how well done this assault is, it definitely is very interesting to see why it is working. Individuals succumb to this trick while endeavoring to keep an unapproved application buy for them.
To keep safe one must be vigilant. The only weakness of this campaign is the use of very suspicious URLs. An observant person will easily see that the URLs are not legitimate, look strange, and should be avoided. For this reason, it is very important that users do not open links from strange emails and instead go directly to a company’s web site. If they do open links from emails, it is always important to analyze the URL of the landing page to make sure you are at a legitimate site.