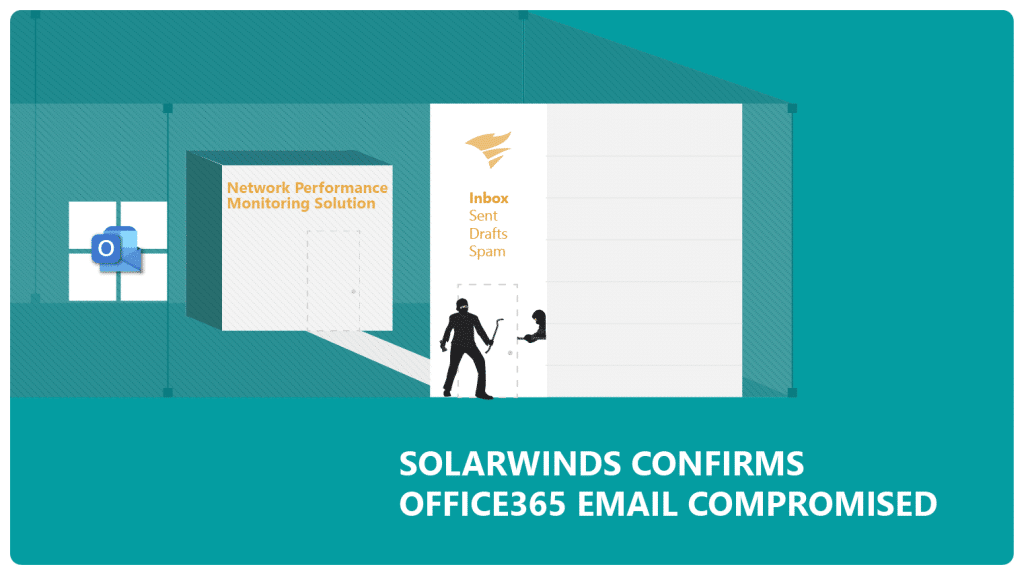
SolarWinds, an IT services company, recently faced issue with their email security. Sudhakar Ramakrishna, CEO SolarWinds, suspects a zero-day vulnerability exploitation in their O365 environment. After the Office365 email compromise, hackers gained illegal access to SolarWinds’ Orion project, which is their network performance monitoring solution.
What were the gaps in Office365 Email Security?
Microsoft is generally very stringent on implementing multi-factor authentication. But this time, the hackers found a way to bypass MFA by supposedly capitalizing on a zero-day vulnerability. Using stolen credentials obtained by third-party jail-breaking tools, the hackers compromised the email account of SolarWinds employees, particularly those in the business and technical roles. However, no specific gaps have been pinpointed after much investigation.
“We’ve confirmed that a SolarWinds email account was compromised and used to programmatically access accounts of targeted SolarWinds personnel in business and technical roles,” Mr. Sudhakar said. “By compromising credentials of SolarWinds employees, the threat actors were able to gain access to and exploit our Orion development environment.”
Although the particular gap which caused the Office365 email compromise is still not clear, security investigators believe the breach of an Office365 email account was the entry point for the hackers to get into the SolarWinds Orion development environment.
Post-attack, the hackers deleted programs to avoid forensic discovery and masked file names and activity to throw on an illusion of legitimate applications and files. One interesting thing to note is that the hackers lay dormant for two weeks upon compromising the O365 email account, before launching the attack. They also used servers which lie outside the monitoring authority of U.S. intelligence, to avoid detection.
SolarWinds Stance on the Office365 Email Compromise
The perpetrators of this attack, SolarWinds suspects, is a group of Russian foreign intelligence agents who definitely have not targeted SolarWinds singularly. The Russian group has gained notoriety for surpassing most security barriers of plenty of other targets before.
SolarWinds concedes that a targeted, nation-state attack is hard to ward off. But rather than wallow, they have done the commendable thing of making an example of their security breach, so that other corporations can become weary and take preventive security measures.
“While it’s widely understood any one company could not protect itself against a sustained and unprecedented nation-state attack of this kind, we see an opportunity to lead an industry-wide effort that makes SolarWinds a model for secure software environments, development processes, and products,” Mr. Sudhakar Ramakrishna writes.
As far as countermeasures go, SolarWinds will opt for stronger endpoint security mechanisms that will supplement Microsoft’s own inherent security provisions. They will ensure an organization-wide MFA implementation and a hierarchy of privilege for access to sensitive data. They will also install a screening of vendors before procuring security services.
Case Study: SolarWinds Battles Against Dark Halo.
What can you learn?
There is no doubt that before the attack, SolarWinds security practices were at par. They were definitely as per industry best practices but still the company fell prey to an attack. This is an invaluable lesson, that you should constantly keep updating your security strength and not remain stagnant with your security.
Another observation here is that this attack targeted the business and technical team of the organization. This is a deviation from usual email security attacks, which target the finance department and decision-makers to siphon off money. What this tells us is that your security measures should span across your company and not just specific departments.
Also note how Microsoft’s name was unnecessarily dragged through the mud. While Microsoft cleverly stopped this case from becoming an issue by declining to give a public comment, you cannot deny that brand trust takes a certain hit when something like this happens. However, SolarWinds has smartly taken a decision to study their vendors before procurement.
Which vendors you choose does make a difference. When it comes to Office365, Logix is a Microsoft Gold Partner. In that capacity, we have the privilege to provide additional advanced email security to the Microsoft offerings we have.
Make wiser decision with your security and reap long-term benefits of better online security.