
Until recently, the industry has relied on basic authentication as a security mechanism to connect to remote and local servers, services, and inter-application APIs. And until recently, it has sufficed, thus not providing any incentive to giants like Microsoft to switch to something more advanced.
However, basic authentication simply means you supply your username and password with your requests, which makes it very vulnerable to interception and theft. Not only are your credentials at risk, your request is also susceptible to being tampered with, causing havoc on the server side.
Also, basic authentication has compatibility issues with Multi-Factor Authentication (MFA) in some cases.
Seeing this, Microsoft decided to take some active steps. Since October 01 2022, Microsoft Basic Authentication has been deprecated and is no longer supported on Exchange Online. Effective October 1st, Microsoft has begun disabling Basic authentication for Outlook, EWS, RPS, POP, IMAP, and EAS protocols in Exchange Online.
What has changed?
Microsoft has removed the ability to use basic authentication in Exchange Online for Exchange ActiveSync (EAS), POP, IMAP, Remote PowerShell, Exchange Web Services (EWS), Offline Address Book (OAB), Outlook for both Windows, and Mac.
They’re also disabling SMTP Auth in all tenants in which it is inactive.
Therefore, customers will need to shift from apps that use basic authentication to ones that implement modern authentication, which works on the basis of OAuth 2.0 token access, which has a short validity lifetime, making it more secure.
Modern authentication also supports MFA easily, making it that much more convenient to use.
Which existing setups will be impacted?
- The following setups and messaging protocols will be impacted:
POP, IMAP, and SMTP AUTH - Exchange ActiveSync (EAS)
- Exchange Online PowerShell
- Exchange Web Services (EWS)
- Outlook, MAPI, RPC, and Offline Address Book (OAB)
How can I know if I am still on Microsoft Basic Authentication?
To check if you are still on basic authentication, you have 4 options.
Authentication Dialogue
Modern authentication uses a web-based login page, like so:
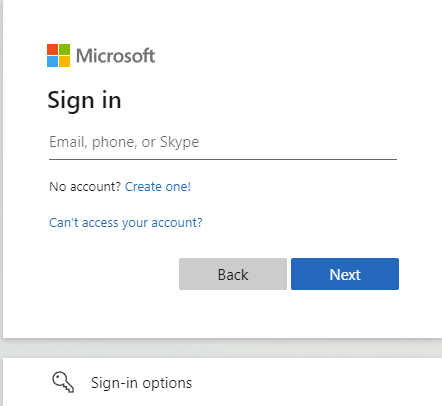
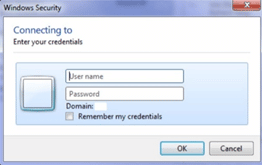
Whereas the basic authentication method uses a credentials-based native dialogue box:
Message Center
Since the end of 2021, Microsoft has been sending Message Center reports to its tenants, with summaries of basic authentication usage. You can scan these reports to know how many users are still using basic authentication and what kind of protocols they are using.
Admin Center
Microsoft is planning to make it easier for administrators to see summary usages and enable or disable protocols right from the Admin Center. Details on this change to be announced.
Azure AD Sign-In Report
The Azure AD (Active Directory) Sign-In report gives the most up-to-date view on basic authentication usage. You can also export the logs to do deeper investigation into your users’ authentication protocols. Azure AD gives a number of options to export logs, including the Azure Event Hubs, Azure Storage, or Azure Monitor, Graph APIs through MS Graph, along with the simplest direct download method from web browsers.
